- Home
The Mandate
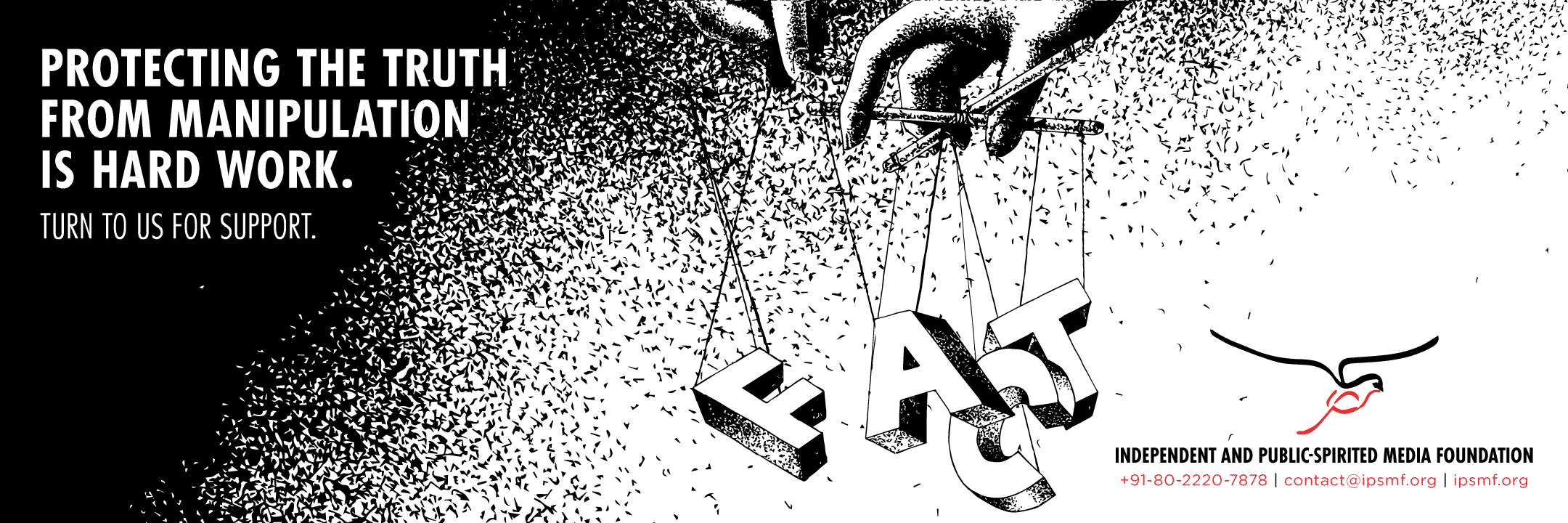
The Foundation Promotes Excellence In Independent, Public-Spirited & Socially Impactful Journalism

Invest
Read MoreIn independent and impactful digital-media entities, In encouraging digital-media ventures to focus on public-interest issues.

Catalyze
Read MoreIn independent and impactful digital-media entities, In encouraging digital-media ventures to focus on public-interest issues.

Grow
Read MoreIn independent and impactful digital-media entities, In encouraging digital-media ventures to focus on public-interest issues.

Influence
Read MoreIn independent and impactful digital-media entities, In encouraging digital-media ventures to focus on public-interest issues.
Funding
Independent Media
since 2015

Vision & Values
The FoundingIndependent And Public-Spirited Media Foundation (IPSMF) is registered as a public charitable trust in Bengaluru on 1 July 2015. The Foundation provides financial support and seeks to mentor digital-media entities in creating and disseminating public-interest information borne out of serious and independent journalism. The Foundation has been registered under Section 12AA (a) of the IT Act, 1961 and has been granted approval under section 80G (5) (vi) of the IT Act, 1961.
The Rationale For The Foundation
- The challenges facing Journalism
- Why Support Public-Interest Journalism?
- The Editor’s Role is Paramount
- Reinventing Media – The Digital Opportunity